
Full jury seated at Trump trial on third day of selection process
Twelve people have been selected to serve as jurors in former President Donald Trump's criminal trial in New York, filling out the panel on the third day of proceedings.
Watch CBS News

Twelve people have been selected to serve as jurors in former President Donald Trump's criminal trial in New York, filling out the panel on the third day of proceedings.

Cuba's deputy foreign minister tells CBS News that his country is willing to accommodate more than one deportation flight per month.

The Supreme Court will consider Monday whether bans on public camping constitute "cruel and unusual punishment" barred by the Eighth Amendment.

House Rules allow a single member to force a vote on ousting the speaker. Conservatives want to keep it that way.

A man who spent more than 20 years in prison for murdering two married Darthmouth College professors back in 2001 has been granted parole.

Rep. Ilhan Omar's daughter says she was one of three students suspended from Barnard College following a pro-Palestinian protest at Columbia University on Thursday.

Italy joins a long list of countries offering foreigners the opportunity to relocate, laptops in tow.

Dubai is known for using planes to help prompt precipitation over the region. But experts say it did not play a role in this week's historic downpour.
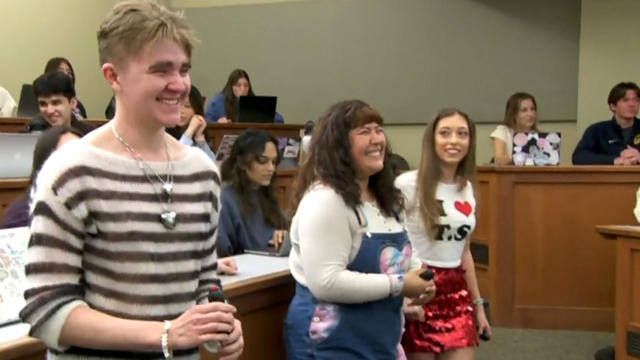
Taylor Swift's successes and failures, including the battle to regain control of her master recordings, are part of the syllabus at the University of California, Berkeley.

Police started making arrests Thursday afternoon at a makeshift encampment that pro-Palestinian protesters had set up on Columbia's quad.

"Their job is to protect our investments," said one man whose bank account was drained of $15,000. "Otherwise, what's the point of putting it with a bank?"

Scientists are using a range of tools to protect the endangered wildlife that could disappear in coming decades.

Two officers survived the plane crash in Elgeyo Marakwet county, about 250 miles northwest of Nairobi, Kenya.

Taylor Swift took to social media hours ahead of the expected release of her new album "The Tortured Poets Department."

A woman fell 140 feet to her death while hiking on Bear Mountain in Sedona, a scenic Arizona mountain town and popular tourist destination.

A concerning video shows a group of people in North Carolina pulling two small bear cubs from a tree in Asheville.

A JetBlue flight was forced to abort takeoff due to another aircraft attempting to cross the runway at Washington Reagan National Airport.

Elections are set to kick off in India, the world's biggest democracy, but there's concern that democratic values are being eroded.

Under the 5th Amendment, the jury is prohibited from holding it against former President Donald Trump if he does not testify.

The jurors are tasked with deciding the outcome of the first criminal trial of a former president in U.S. history.

The case stems from a "hush money" payment of $130,000 to adult film star Stormy Daniels in 2016.

Several of Robert F. Kennedy Jr.'s brothers and sisters endorsed the president, even as their brother makes his own bid for Biden's job.

Former President Donald Trump met Wednesday in New York with Polish President Andrzej Duda, the latest in a series of meetings with foreign leaders as Europe braces for the possibility of a second Trump term.

The allies want the leaders to reconnect ahead of another potential Trump term, sources confirm.

After Israel accused the U.N. of failing to "do its job," the head of a U.N. aid agency says it's Israel delaying the flow of food to those in need.

UNICEF says a third of Gaza's infants and toddlers are acutely malnourished, but Israel blames the U.N. itself.

Details emerge of Iran's unprecedented direct attack on Israel, and how it was largely thwarted by the U.S. ally's defenses.
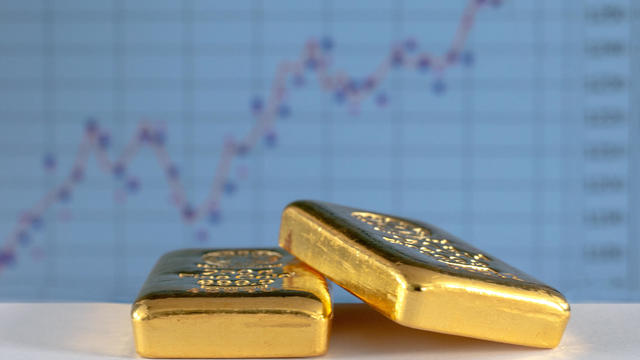
Both types of gold assets could be a smart bet in today's economic environment. Here's why.

Considering tapping into your home equity? Here's how much you'd save when compared to your other options.

Are you shopping for long-term care insurance in your 70s? Make these three smart moves.

Italy joins a long list of countries offering foreigners the opportunity to relocate, laptops in tow.

Tesla's stock price has tumbled 39% this year amid concerns about the electric vehicle maker's slowing growth.

Health officials are warning consumers not to consume the Infinite Herbs basil sold at Trader Joe's after 12 people were sickened.

Nine workers arrested after demonstrations at the tech giant's offices n New York and California.

The U.S. is reaching "peak 65," marking the largest retirement wave in American history. But the financial outlook for many is grim.

From Hey Dude shoes to a luxury toilet upgrade, Sam's Club shoppers are going wild for these trending products.

Find that special someone by signing up for one of the undeniably best dating apps in 2024.

Hate mowing your lawn? Well now you can let a robot do it for you. Check out these latest robotic lawn mowers.

A full jury of seven men and five women have been seated for former President Donald Trump's Manhattan trial, in which he is accused of falsifying business records to hide an alleged affair ahead of the 2016 election. Robert Costa has more.

Police in riot gear detained pro-Palestinian protesters at Columbia University in Manhattan Thursday, loading them into multiple busses. Several participating students were suspended, including the daughter of Rep. Ilhan Omar, who was suspended by Barnard College. Lilia Luciano has more.

Embattled House Speaker Mike Johnson is trying to stop a revolt among his fellow Republicans while winning support for his plan to provide military funding to Ukraine ahead of a possible vote Saturday. The chair of the Senate Commerce Committee has also thrown her support behind a bill that could lead to a U.S. ban of TikTok. Scott MacFarlane has the latest.

President Biden held a campaign event with 15 members of the Kennedy family Thursday, as they threw their support behind Mr. Biden instead of their own relative, Robert F. Kennedy, Jr. His family's public endorsement of Mr. Biden signals how seriously Democrats are taking his run. Nikole Killion has details.

A full jury of seven men and five women have been seated for former President Donald Trump's Manhattan trial, in which he is accused of falsifying business records to hide an alleged affair ahead of the 2016 election. Robert Costa has more.

Police in riot gear detained pro-Palestinian protesters at Columbia University in Manhattan Thursday, loading them into multiple busses. Several participating students were suspended, including the daughter of Rep. Ilhan Omar, who was suspended by Barnard College. Lilia Luciano has more.

Embattled House Speaker Mike Johnson is trying to stop a revolt among his fellow Republicans while winning support for his plan to provide military funding to Ukraine ahead of a possible vote Saturday. The chair of the Senate Commerce Committee has also thrown her support behind a bill that could lead to a U.S. ban of TikTok. Scott MacFarlane has the latest.

Earlier this week, a staggering 10 inches of rain fell in the United Arab Emirates, the most the UAE has seen in a single storm in 75 years. The rainfall shuttered schools, destroyed homes and cripped Dubai International Airport, the world's second-busiest hub. The airport is now slowly reopening. Chris Livesay has the latest.

A new court filing from attorneys representing Bryan Kohberger, the man charged with killing four University of Idaho students in November 2022, alleges that cell phone tower data shows that Kohberger was not at the murder scene on the night of the slayings. Carter Evans has details.

The significance of the song was amplified by praise from music legend Paul McCartney, who called the recording "magnificent" and appreciated its reinforcement of the civil rights message he intended when writing "Blackbird."

The singers first dated in 2003 and delighted fans when they rekindled their relationship in 2023.

A landmark review for Britain's National Health Service found young people have been let down by "remarkably weak" evidence backing medical interventions in gender care.

Jay Jurden's star has been on the rise for the last few years, landing him on multiple "Comics to Watch" lists. He was a writer on the Apple TV Plus show "The Problem with Jon Stewart." His comedy album "Jay Jurden, Y'all" debuted at No. 1 on iTunes in 2020. We asked the up-and-coming comedian to meet us at one of his favorite spots for his first TV interview — and for a little surprise.

After gaining significant attention from being featured on Beyoncé's "Cowboy Carter," rising country artist Brittney Spencer joins "CBS Mornings" to talk about her rise to fame.

U.S. officials, from the president to the Treasury secretary, are accusing China of pushing cheap goods. Mark Wu, professor of law at Harvard University, joins CBS News to examine how low-priced Chinese products could impact American businesses, workers and the global economy.

Some of the most critically endangered birds on the planet have been released back into the wild. CBS News national environmental correspondent David Schechter has more on the harsh conditions Puerto Rican parrots face, and the people working to save them.

A bipartisan group of lawmakers has introduced a bill supporting the development of nuclear fusion power. Hank Jenkins-Smith, professor of public policy at the University of Oklahoma, joins CBS News to discuss.

House Speaker Mike Johnson is bundling the bill that could lead to a ban on TikTok into his four-part foreign aid plan. The legislation would require TikTok's Chinese owner, ByteDance, to sell the popular social media network or face a ban in the U.S. CBS News congressional correspondent Scott MacFarlane has more.

Twelve jurors have been selected in former President Donald Trump's "hush money" criminal case. CBS News chief election and campaign correspondent Robert Costa explains what happens next.

Spencer, the official mascot of the Boston Marathon, is honored by his community. David Begnaud introduces us to a woman who calls herself a "bad weather friend" – because she's there when you need her most. Plus, more heartwarming stories.

Russ Cook says the scariest part of his run through Africa was "on the back of a motorbike, thinking I was about to die."

A trendsetting third grader creates a school tradition to don dapper outfits on Wednesdays. A retiree makes it her mission to thank those who may be in thankless jobs. Plus, more heartwarming and inspiring stories.

Lyn Story is a retiree whose mission is to be the "bad weather friend," someone who is there for you in a time of need. David Begnaud shows how her huge heart led to life-changing friendships.

Nets star Mikal Bridges fulfills his dream of teaching by working at a school in Brooklyn for the day. A doctor overcomes the odds to help other survivors of catastrophic injuries. Plus, behind the scenes of Drew Barrymore's talk show, and more heartwarming stories.

CBS Reports goes to Illinois, which has one of the highest rates of institutionalization in the country, to understand the challenges families face keeping their developmentally disabled loved ones at home.

As more states legalize gambling, online sportsbooks have spent billions courting the next generation of bettors. And now, as mobile apps offer 24/7 access to placing wagers, addiction groups say more young people are seeking help than ever before. CBS Reports explores what experts say is a hidden epidemic lurking behind a sports betting bonanza that's leaving a trail of broken lives.

In February 2023, a quiet community in Ohio was blindsided by disaster when a train derailed and authorities decided to unleash a plume of toxic smoke in an attempt to avoid an explosion. Days later, residents and the media thought the story was over, but in fact it was just beginning. What unfolded in East Palestine is a cautionary tale for every town and city in America.

In the aftermath of the Supreme Court striking down affirmative action in college admissions, CBS Reports examines the fog of uncertainty for students and administrators who say the decision threatens to unravel decades of progress.

CBS Reports examines the legacy of the U.S. government's terrorist watchlist, 20 years after its inception. In the years since 9/11, the database has grown exponentially to target an estimated 2 million people, while those who believe they were wrongfully added are struggling to clear their names.
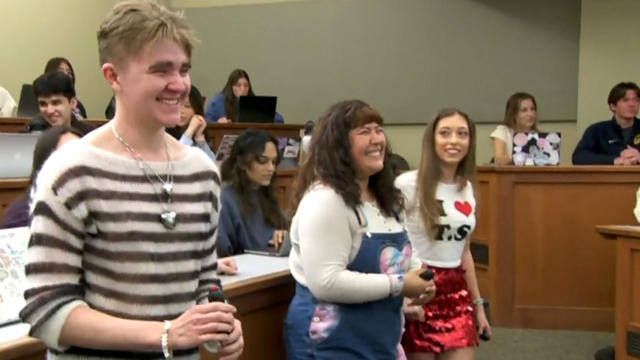
Taylor Swift's successes and failures, including the battle to regain control of her master recordings, are part of the syllabus at the University of California, Berkeley.

Prosecutors allege one of the suspects, Tifany Adams, provided a statement to law enforcement "indicating her responsibility" in the killings.

"Their job is to protect our investments," said one man whose bank account was drained of $15,000. "Otherwise, what's the point of putting it with a bank?"

Online furniture and home furnishings seller says it is opening a brick-and-mortar location in May.

House Rules allow a single member to force a vote on ousting the speaker. Conservatives want to keep it that way.

"Their job is to protect our investments," said one man whose bank account was drained of $15,000. "Otherwise, what's the point of putting it with a bank?"

Online furniture and home furnishings seller says it is opening a brick-and-mortar location in May.

Tesla's stock price has tumbled 39% this year amid concerns about the electric vehicle maker's slowing growth.

Italy joins a long list of countries offering foreigners the opportunity to relocate, laptops in tow.

Sen. Maria Cantwell is backing an amended bill that could lead to a ban of TikTok in the U.S.

Rep. Ilhan Omar's daughter says she was one of three students suspended from Barnard College following a pro-Palestinian protest at Columbia University on Thursday.

House Rules allow a single member to force a vote on ousting the speaker. Conservatives want to keep it that way.

Cuba's deputy foreign minister tells CBS News that his country is willing to accommodate more than one deportation flight per month.

Police arrested more than 100 people at Columbia University on Thursday at a makeshift encampment set up by pro-Palestinian protesters on the university's main lawn.

Sen. Maria Cantwell is backing an amended bill that could lead to a ban of TikTok in the U.S.

Health officials are warning consumers not to consume the Infinite Herbs basil sold at Trader Joe's after 12 people were sickened.

A landmark review for Britain's National Health Service found young people have been let down by "remarkably weak" evidence backing medical interventions in gender care.

Organic option is best when buying certain produce, especially blueberries, nonprofit group says in analysis of chemical residues.

British lawmakers have backed legislation that would see the legal age to buy tobacco increase by one year every year until it's eventually banned.

A new generation of deodorant products promise whole-body odor protection. Should you try one? Dermatologists share what to know.

Cuba's deputy foreign minister tells CBS News that his country is willing to accommodate more than one deportation flight per month.

Two officers survived the plane crash in Elgeyo Marakwet county, about 250 miles northwest of Nairobi, Kenya.

Elections are set to kick off in India, the world's biggest democracy, but there's concern that democratic values are being eroded.

After Israel accused the U.N. of failing to "do its job," the head of a U.N. aid agency says it's Israel delaying the flow of food to those in need.

Police arrested more than 100 people at Columbia University on Thursday at a makeshift encampment set up by pro-Palestinian protesters on the university's main lawn.
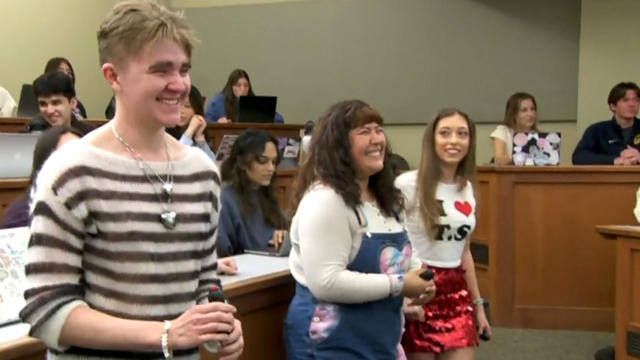
Taylor Swift's successes and failures, including the battle to regain control of her master recordings, are part of the syllabus at the University of California, Berkeley.
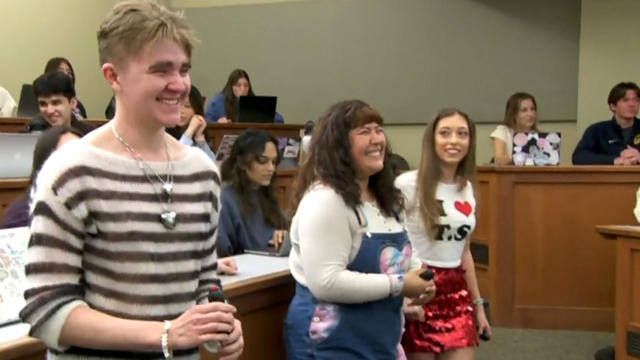
Taylor Swift's successes and failures, including the battle to regain control of her master recordings, are part of the syllabus at the University of California, Berkeley. Jo Ling Kent has more.

Dickey Betts, a guitarist and founding member of the Allman Brothers Band, has died at the age of 80 following a battle with cancer. Betts wrote some of the bands biggest hits, including "Ramblin' Man."

Taylor Swift took to social media hours ahead of the expected release of her new album "The Tortured Poets Department."

Guitar legend Dickey Betts, who co-founded the Allman Brothers Band and wrote their biggest hit, "Ramblin' Man," has died.

A bipartisan group of lawmakers has introduced a bill supporting the development of nuclear fusion power. Hank Jenkins-Smith, professor of public policy at the University of Oklahoma, joins CBS News to discuss.

Sen. Maria Cantwell is backing an amended bill that could lead to a ban of TikTok in the U.S.

From labor shortages to environmental impacts, farmers are looking to AI to help revolutionize the agriculture industry. One California startup, Farm-ng, is tapping into the power of AI and robotics to perform a wide range of tasks, including seeding, weeding and harvesting.

U.S. Senators are pressing banks to take more actions to help victims of wire fraud. CBS News national consumer investigative correspondent Anna Werner has more on how Americans are being scammed.

Artificial intelligence has become so advanced it has now surpassed human performance in several basic tasks, according to a new report from Stanford University's Institute for Human-Centered Artificial Intelligence. Russell Wald, deputy director of the institute, joins CBS News to unpack more key findings from the study.

Some of the most critically endangered birds on the planet have been released back into the wild. CBS News national environmental correspondent David Schechter has more on the harsh conditions Puerto Rican parrots face, and the people working to save them.

Scientists are using a range of tools to protect the endangered wildlife that could disappear in coming decades.

A human jawbone containing several teeth was linked to a former U.S. Marine who died almost 75 years ago during a military exercise in California.

The recent births of Noreen and Antonia are boosting hopes of diversifying the endangered species.

Hurricane Maria nearly wiped out an endangered parrot in Puerto Rico, highlighting the grave threat climate change-fueled storms pose to endangered species.

Prosecutors allege one of the suspects, Tifany Adams, provided a statement to law enforcement "indicating her responsibility" in the killings.

The man faces seven charges related to drug importation and dealing and 12 other charges. He faces life in prison, officials said.

Twelve people have been selected to serve as jurors in former President Donald Trump's criminal trial in New York, filling out the panel on the third day of proceedings.

Sgt. Tony Anthony Mason Jr. was shot to death while sitting in a car with a woman he had been dating, according to police.

In an alibli court filing, lawyers for Bryan Kohberger, accused of fatally stabbing four University of Idaho students, claim he was "out driving" the night of the killings.

NASA confirmed Monday that a mystery object that crashed through the roof of a Naples, Florida home last month was space junk from equipment discarded by the space station.
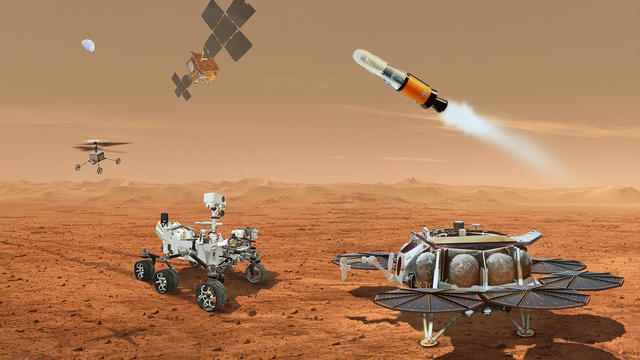
NASA said it agrees with an independent review board that concluded the project could cost up to $11 billion without major changes.

It was a "bittersweet moment" as United Launch Alliance brought the Delta program to a close.

NASA flight engineers managed to photograph and videotape the moon's shadow on Earth about 260 miles below them.

Millions of Americans poured into the solar eclipse’s path of totality to watch in wonder. The excitement was shared across generations for the rare celestial event that saw watch parties across the country as almost all of the continental U.S. saw at least a partial solar eclipse.

A look back at the esteemed personalities who've left us this year, who'd touched us with their innovation, creativity and humanity.

The Francis Scott Key Bridge in Baltimore collapsed early Tuesday, March 26 after a column was struck by a container ship that reportedly lost power, sending vehicles and people into the Patapsco River.

When Tiffiney Crawford was found dead inside her van, authorities believed she might have taken her own life. But could she shoot herself twice in the head with her non-dominant hand?

We look back at the life and career of the longtime host of "Sunday Morning," and "one of the most enduring and most endearing" people in broadcasting.

Cayley Mandadi's mother and stepfather go to extreme lengths to prove her death was no accident.
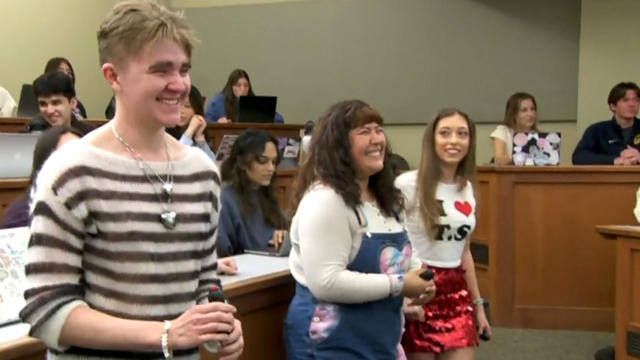
Taylor Swift's successes and failures, including the battle to regain control of her master recordings, are part of the syllabus at the University of California, Berkeley. Jo Ling Kent has more.

U.S. officials, from the president to the Treasury secretary, are accusing China of pushing cheap goods. Mark Wu, professor of law at Harvard University, joins CBS News to examine how low-priced Chinese products could impact American businesses, workers and the global economy.

Some of the most critically endangered birds on the planet have been released back into the wild. CBS News national environmental correspondent David Schechter has more on the harsh conditions Puerto Rican parrots face, and the people working to save them.

A bipartisan group of lawmakers has introduced a bill supporting the development of nuclear fusion power. Hank Jenkins-Smith, professor of public policy at the University of Oklahoma, joins CBS News to discuss.

House Speaker Mike Johnson is bundling the bill that could lead to a ban on TikTok into his four-part foreign aid plan. The legislation would require TikTok's Chinese owner, ByteDance, to sell the popular social media network or face a ban in the U.S. CBS News congressional correspondent Scott MacFarlane has more.