
Tehran downplays strike as U.S. officials say Israeli missile hit Iran
Two U.S. officials tell CBS News an Israeli missile has hit Iran in apparent retaliation for the recent drone and missile attack on the Jewish state.
Watch CBS News

Two U.S. officials tell CBS News an Israeli missile has hit Iran in apparent retaliation for the recent drone and missile attack on the Jewish state.

Twelve jurors and one alternate were seated in the first three days of jury selection in former President Donald Trump's New York criminal trial.

Maxwell Anderson, 33, has been charged with first-degree intentional homicide in the death of 19-year-old Sade Robinson.

A German prosecutor says 2 German-Russian nationals were caught snooping around U.S. military facilities used to train Ukrainian forces.

The bills are part of a complicated plan by Speaker Mike Johnson to get badly needed lethal aid to Ukraine, as well as security funding for Israel and Taiwan.

His comments come as a deadlocked Congress continues to stall on Ukraine aid.

Anticipation was growing at a fever pitch before Taylor Swift's latest album, "The Tortured Poets Department," dropped at midnight EDT. But it turned out it's actually a double album.
The Vasuki indicus specimen dates back 47 million years and is more than double the average size of similar snakes, like pythons.

A driver died after his vehicle plunged over a cliff along Highway 1 on the San Francisco Peninsula coast between Pacifica and Half Moon Bay Thursday.

A disappearing lizard population in the mountains of Arizona shows how climate change is fast-tracking the rate of extinction.

Dennis Dechaine is serving a life sentence for the murder and sexual assault of Sarah Cherry, who disappeared while babysitting in 1988.

"Their job is to protect our investments," said one man whose bank account was drained of $15,000. "Otherwise, what's the point of putting it with a bank?"

Direct conflict between Israel and Iran, which threaten global oil supplies and could drive up energy costs, has investors on edge.

Police arrested more than 100 people at Columbia University on Thursday at a makeshift encampment set up by pro-Palestinian protesters on the university's main lawn.
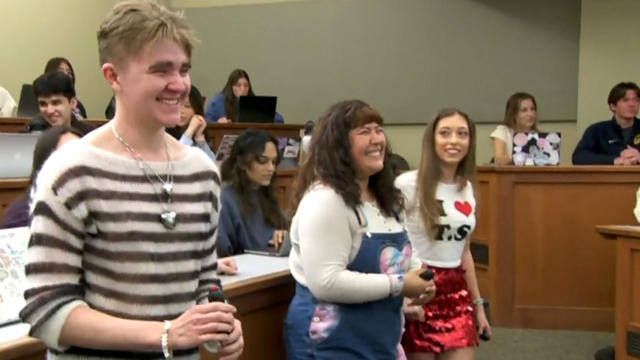
Taylor Swift's successes and failures, including the battle to regain control of her master recordings, are part of the syllabus at the University of California, Berkeley.

House Rules allow a single member to force a vote on ousting the speaker. Conservatives want to keep it that way.

A JetBlue flight was forced to abort takeoff due to another aircraft attempting to cross the runway at Washington Reagan National Airport.

A concerning video shows a group of people in North Carolina pulling two small bear cubs from a tree in Asheville.

Twelve people have been selected to serve as jurors in former President Donald Trump's criminal trial in New York, filling out the panel on the third day of proceedings.

Under the 5th Amendment, the jury is prohibited from holding it against former President Donald Trump if he does not testify.

The jurors are tasked with deciding the outcome of the first criminal trial of a former president in U.S. history.

They backed the president even as their brother makes his own bid for Biden's job.

It came with Europe bracing for the possibility of a second Trump term.

The allies want the leaders to reconnect ahead of another potential Trump term, sources confirm.

Rep. Ilhan Omar's daughter says she was one of three students suspended from Barnard College.

After Israel accused the U.N. of failing to "do its job," the head of a U.N. aid agency said it's Israel that's delaying the flow.

UNICEF says a third of Gaza's infants and toddlers are acutely malnourished, but Israel blames the U.N. itself.
Both types of gold assets could be a smart bet in today's economic environment. Here's why.

Considering tapping into your home equity? Here's how much you'd save when compared to your other options.

Are you shopping for long-term care insurance in your 70s? Make these three smart moves.

Direct conflict between Israel and Iran, which threaten global oil supplies and could drive up energy costs, has investors on edge.

Online furniture and home furnishings seller says it is opening a brick-and-mortar location in May.

Italy joins a long list of countries offering foreigners the opportunity to relocate, laptops in tow.

Tesla's stock price has tumbled 39% this year amid concerns about the electric vehicle maker's slowing growth.

Health officials are warning consumers not to consume the Infinite Herbs basil sold at Trader Joe's after 12 people were sickened.

From Hey Dude shoes to a luxury toilet upgrade, Sam's Club shoppers are going wild for these trending products.

Can't decide between a laptop and tablet? Consider getting one device with the functionality of both.

Find out how and when to watch the US Open Pickleball Championships, including who's competing.
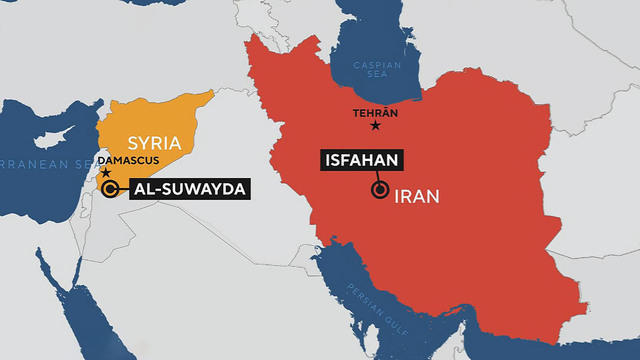
Israel launches a strike on Iran, risking a wider war. Also, two jets nearly collide on a busy U.S. airport runway. All that and all that matters in today’s Eye Opener.

CBS News' data analysis found 425 bridges in 36 states over waterways used by large vessels had inadequate pier protection.

A JetBlue flight from Washington to Boston began to take off at the same time a Southwest jet was crossing the same runway. Both planes stopped moments before a potential collision.

All 12 jurors have been selected in former President Donald Trump’s “hush money” trial. Trump, who has pleaded not guilty to all charges, is accused of falsifying business records to hide an alleged affair with an adult film actor ahead of the 2016 election. The trial could begin as soon as Monday.

In "Kindness 101," where Steve Hartman and his children share stories built around kindness and character, and the people who've mastered those qualities. Today's lesson is purpose. This week, we find out how one widower was able to find a new purpose in life from an unlikely source.

CBS News' data analysis found 425 bridges in 36 states over waterways used by large vessels had inadequate pier protection.

A report from the United Nations determined that 1 million species are threatened with extinction. Dr. John Wiens from the University of Arizona believes that number is far higher based on his research. He says climate change is quickening the threat of extinction for species, including a 3-million-year-old lizard population previously found in the Arizona mountains.

Legendary guitarist Dickey Betts died Thursday at his home in Florida after battling cancer. The Rock ‘N Roll Hall of Famer was 80 years old.

All 12 jurors have been selected in former President Donald Trump’s “hush money” trial. Trump, who has pleaded not guilty to all charges, is accused of falsifying business records to hide an alleged affair with an adult film actor ahead of the 2016 election. The trial could begin as soon as Monday.

Starbucks unveiled the new cups ahead of Earth Day and as a new report warns plastic production emissions are even greater than those from aviation.

The significance of the song was amplified by praise from music legend Paul McCartney, who called the recording "magnificent" and appreciated its reinforcement of the civil rights message he intended when writing "Blackbird."

The singers first dated in 2003 and delighted fans when they rekindled their relationship in 2023.

A landmark review for Britain's National Health Service found young people have been let down by "remarkably weak" evidence backing medical interventions in gender care.

Jay Jurden's star has been on the rise for the last few years, landing him on multiple "Comics to Watch" lists. He was a writer on the Apple TV Plus show "The Problem with Jon Stewart." His comedy album "Jay Jurden, Y'all" debuted at No. 1 on iTunes in 2020. We asked the up-and-coming comedian to meet us at one of his favorite spots for his first TV interview — and for a little surprise.

Anderson Cooper profiles Kevin Hart, the highest-grossing comedian today and a bankable movie star, who has added a new title to his resume – entertainment and business mogul. 60 Minutes, Sunday.

Less than 100 miles from Britain’s mainland lie the Channel Islands, British Crown dependencies with a hotly debated history. The islands were occupied by Germany during World War II and the Nazis operated two concentration camps there. Sunday.

Since taking office as the U.S. Secretary of Commerce under the Biden administration, Gina Raimondo has turned the second-tier agency into a center of national security, manufacturing, and job creation. Sunday.

Acclaimed author Salman Rushdie says the attack on free expression now comes from both the left and the right.

Jon DiMaggio, a former intelligence community analyst and current cybersecurity strategist, has used fake personas to communicate with ransomware gangs on the dark web, finding out who's behind them and how they work.

Spencer, the official mascot of the Boston Marathon, is honored by his community. David Begnaud introduces us to a woman who calls herself a "bad weather friend" – because she's there when you need her most. Plus, more heartwarming stories.

Russ Cook says the scariest part of his run through Africa was "on the back of a motorbike, thinking I was about to die."

A trendsetting third grader creates a school tradition to don dapper outfits on Wednesdays. A retiree makes it her mission to thank those who may be in thankless jobs. Plus, more heartwarming and inspiring stories.

Lyn Story is a retiree whose mission is to be the "bad weather friend," someone who is there for you in a time of need. David Begnaud shows how her huge heart led to life-changing friendships.

Nets star Mikal Bridges fulfills his dream of teaching by working at a school in Brooklyn for the day. A doctor overcomes the odds to help other survivors of catastrophic injuries. Plus, behind the scenes of Drew Barrymore's talk show, and more heartwarming stories.

CBS Reports goes to Illinois, which has one of the highest rates of institutionalization in the country, to understand the challenges families face keeping their developmentally disabled loved ones at home.

As more states legalize gambling, online sportsbooks have spent billions courting the next generation of bettors. And now, as mobile apps offer 24/7 access to placing wagers, addiction groups say more young people are seeking help than ever before. CBS Reports explores what experts say is a hidden epidemic lurking behind a sports betting bonanza that's leaving a trail of broken lives.

In February 2023, a quiet community in Ohio was blindsided by disaster when a train derailed and authorities decided to unleash a plume of toxic smoke in an attempt to avoid an explosion. Days later, residents and the media thought the story was over, but in fact it was just beginning. What unfolded in East Palestine is a cautionary tale for every town and city in America.

In the aftermath of the Supreme Court striking down affirmative action in college admissions, CBS Reports examines the fog of uncertainty for students and administrators who say the decision threatens to unravel decades of progress.

CBS Reports examines the legacy of the U.S. government's terrorist watchlist, 20 years after its inception. In the years since 9/11, the database has grown exponentially to target an estimated 2 million people, while those who believe they were wrongfully added are struggling to clear their names.

Starbucks unveiled the new cups ahead of Earth Day and as a new report warns plastic production emissions are even greater than those from aviation.

The Vasuki indicus specimen dates back 47 million years and is more than double the average size of similar snakes, like pythons.

A look at the features for this week's broadcast of the 2023 News & Documentary Emmy-winner for Outstanding Recorded News Program, hosted by Jane Pauley.

Direct conflict between Israel and Iran, which threaten global oil supplies and could drive up energy costs, has investors on edge.

Twelve jurors and one alternate were seated in the first three days of jury selection in former President Donald Trump's New York criminal trial.

Starbucks unveiled the new cups ahead of Earth Day and as a new report warns plastic production emissions are even greater than those from aviation.

Direct conflict between Israel and Iran, which threaten global oil supplies and could drive up energy costs, has investors on edge.

CEO Mark Zuckerberg's newest AI-powered Meta AI agents started venturing into social media this week to engage with real people.

"Ultimately we think this is a better approach that reflects the evolution of the business," Netflix Co-CEO Greg Peters said on an earnings call.

"Their job is to protect our investments," said one man whose bank account was drained of $15,000. "Otherwise, what's the point of putting it with a bank?"

Twelve jurors and one alternate were seated in the first three days of jury selection in former President Donald Trump's New York criminal trial.

The bills are part of a complicated plan by Speaker Mike Johnson to get badly needed lethal aid to Ukraine, as well as security funding for Israel and Taiwan.

His comments come as a deadlocked Congress continues to stall on Ukraine aid.

Two U.S. officials tell CBS News an Israeli missile has hit Iran in apparent retaliation for the recent drone and missile attack on the Jewish state.

Rep. Ilhan Omar's daughter says she was one of three students suspended from Barnard College following a pro-Palestinian protest at Columbia University on Thursday.

Health officials are warning consumers not to consume the Infinite Herbs basil sold at Trader Joe's after 12 people were sickened.

A landmark review for Britain's National Health Service found young people have been let down by "remarkably weak" evidence backing medical interventions in gender care.

Organic option is best when buying certain produce, especially blueberries, nonprofit group says in analysis of chemical residues.

British lawmakers have backed legislation that would see the legal age to buy tobacco increase by one year every year until it's eventually banned.

A new generation of deodorant products promise whole-body odor protection. Should you try one? Dermatologists share what to know.

The Vasuki indicus specimen dates back 47 million years and is more than double the average size of similar snakes, like pythons.

Paris police cordoned off an area around an Iranian consulate amid reports of a man threatening to detonate a bomb, but a suspect was quickly detained.

A German prosecutor says 2 German-Russian nationals were caught snooping around U.S. military facilities used to train Ukrainian forces.

The bills are part of a complicated plan by Speaker Mike Johnson to get badly needed lethal aid to Ukraine, as well as security funding for Israel and Taiwan.

His comments come as a deadlocked Congress continues to stall on Ukraine aid.

Legendary guitarist Dickey Betts died Thursday at his home in Florida after battling cancer. The Rock ‘N Roll Hall of Famer was 80 years old.

"Ultimately we think this is a better approach that reflects the evolution of the business," Netflix Co-CEO Greg Peters said on an earnings call.
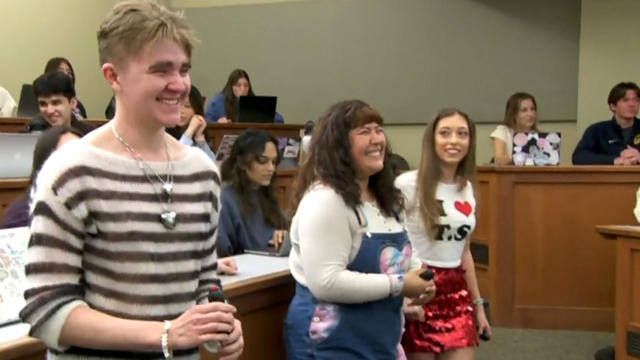
Taylor Swift's successes and failures, including the battle to regain control of her master recordings, are part of the syllabus at the University of California, Berkeley.
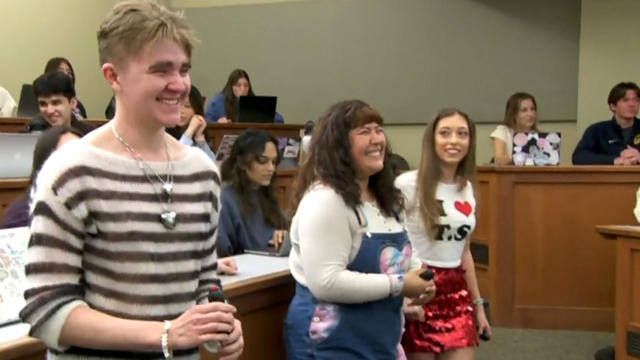
Taylor Swift's successes and failures, including the battle to regain control of her master recordings, are part of the syllabus at the University of California, Berkeley. Jo Ling Kent has more.

Dickey Betts, a guitarist and founding member of the Allman Brothers Band, has died at the age of 80 following a battle with cancer. Betts wrote some of the bands biggest hits, including "Ramblin' Man."

A bipartisan group of lawmakers has introduced a bill supporting the development of nuclear fusion power. Hank Jenkins-Smith, professor of public policy at the University of Oklahoma, joins CBS News to discuss.

Sen. Maria Cantwell is backing an amended bill that could lead to a ban of TikTok in the U.S.

From labor shortages to environmental impacts, farmers are looking to AI to help revolutionize the agriculture industry. One California startup, Farm-ng, is tapping into the power of AI and robotics to perform a wide range of tasks, including seeding, weeding and harvesting.

U.S. Senators are pressing banks to take more actions to help victims of wire fraud. CBS News national consumer investigative correspondent Anna Werner has more on how Americans are being scammed.

Artificial intelligence has become so advanced it has now surpassed human performance in several basic tasks, according to a new report from Stanford University's Institute for Human-Centered Artificial Intelligence. Russell Wald, deputy director of the institute, joins CBS News to unpack more key findings from the study.

Starbucks unveiled the new cups ahead of Earth Day and as a new report warns plastic production emissions are even greater than those from aviation.

A report from the United Nations determined that 1 million species are threatened with extinction. Dr. John Wiens from the University of Arizona believes that number is far higher based on his research. He says climate change is quickening the threat of extinction for species, including a 3-million-year-old lizard population previously found in the Arizona mountains.

A disappearing lizard population in the mountains of Arizona shows how climate change is fast-tracking the rate of extinction.

Some of the most critically endangered birds on the planet have been released back into the wild. CBS News national environmental correspondent David Schechter has more on the harsh conditions Puerto Rican parrots face, and the people working to save them.

Scientists are using a range of tools to protect the endangered wildlife that could disappear in coming decades.

Twelve jurors and one alternate were seated in the first three days of jury selection in former President Donald Trump's New York criminal trial.

Maxwell Anderson, 33, has been charged with first-degree intentional homicide in the death of 19-year-old Sade Robinson.

Dennis Dechaine is serving a life sentence for the murder and sexual assault of Sarah Cherry, who disappeared while babysitting in 1988.

Prosecutors allege one of the suspects, Tifany Adams, provided a statement to law enforcement "indicating her responsibility" in the killings.

The man faces seven charges related to drug importation and dealing and 12 other charges. He faces life in prison, officials said.

NASA confirmed Monday that a mystery object that crashed through the roof of a Naples, Florida home last month was space junk from equipment discarded by the space station.
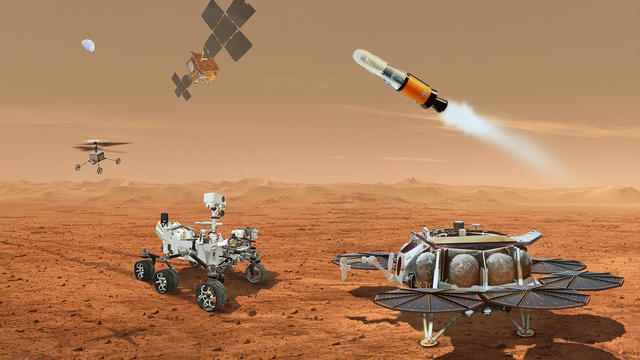
NASA said it agrees with an independent review board that concluded the project could cost up to $11 billion without major changes.

It was a "bittersweet moment" as United Launch Alliance brought the Delta program to a close.

NASA flight engineers managed to photograph and videotape the moon's shadow on Earth about 260 miles below them.

Millions of Americans poured into the solar eclipse’s path of totality to watch in wonder. The excitement was shared across generations for the rare celestial event that saw watch parties across the country as almost all of the continental U.S. saw at least a partial solar eclipse.

A look back at the esteemed personalities who've left us this year, who'd touched us with their innovation, creativity and humanity.

The Francis Scott Key Bridge in Baltimore collapsed early Tuesday, March 26 after a column was struck by a container ship that reportedly lost power, sending vehicles and people into the Patapsco River.

When Tiffiney Crawford was found dead inside her van, authorities believed she might have taken her own life. But could she shoot herself twice in the head with her non-dominant hand?

We look back at the life and career of the longtime host of "Sunday Morning," and "one of the most enduring and most endearing" people in broadcasting.

Cayley Mandadi's mother and stepfather go to extreme lengths to prove her death was no accident.

In "Kindness 101," where Steve Hartman and his children share stories built around kindness and character, and the people who've mastered those qualities. Today's lesson is purpose. This week, we find out how one widower was able to find a new purpose in life from an unlikely source.

CBS News' data analysis found 425 bridges in 36 states over waterways used by large vessels had inadequate pier protection.

A report from the United Nations determined that 1 million species are threatened with extinction. Dr. John Wiens from the University of Arizona believes that number is far higher based on his research. He says climate change is quickening the threat of extinction for species, including a 3-million-year-old lizard population previously found in the Arizona mountains.

Legendary guitarist Dickey Betts died Thursday at his home in Florida after battling cancer. The Rock ‘N Roll Hall of Famer was 80 years old.

All 12 jurors have been selected in former President Donald Trump’s “hush money” trial. Trump, who has pleaded not guilty to all charges, is accused of falsifying business records to hide an alleged affair with an adult film actor ahead of the 2016 election. The trial could begin as soon as Monday.